Breach Of Contract Law Dictionary Line Icon Vector Illustration Stock Illustration - Download Image Now - iStock

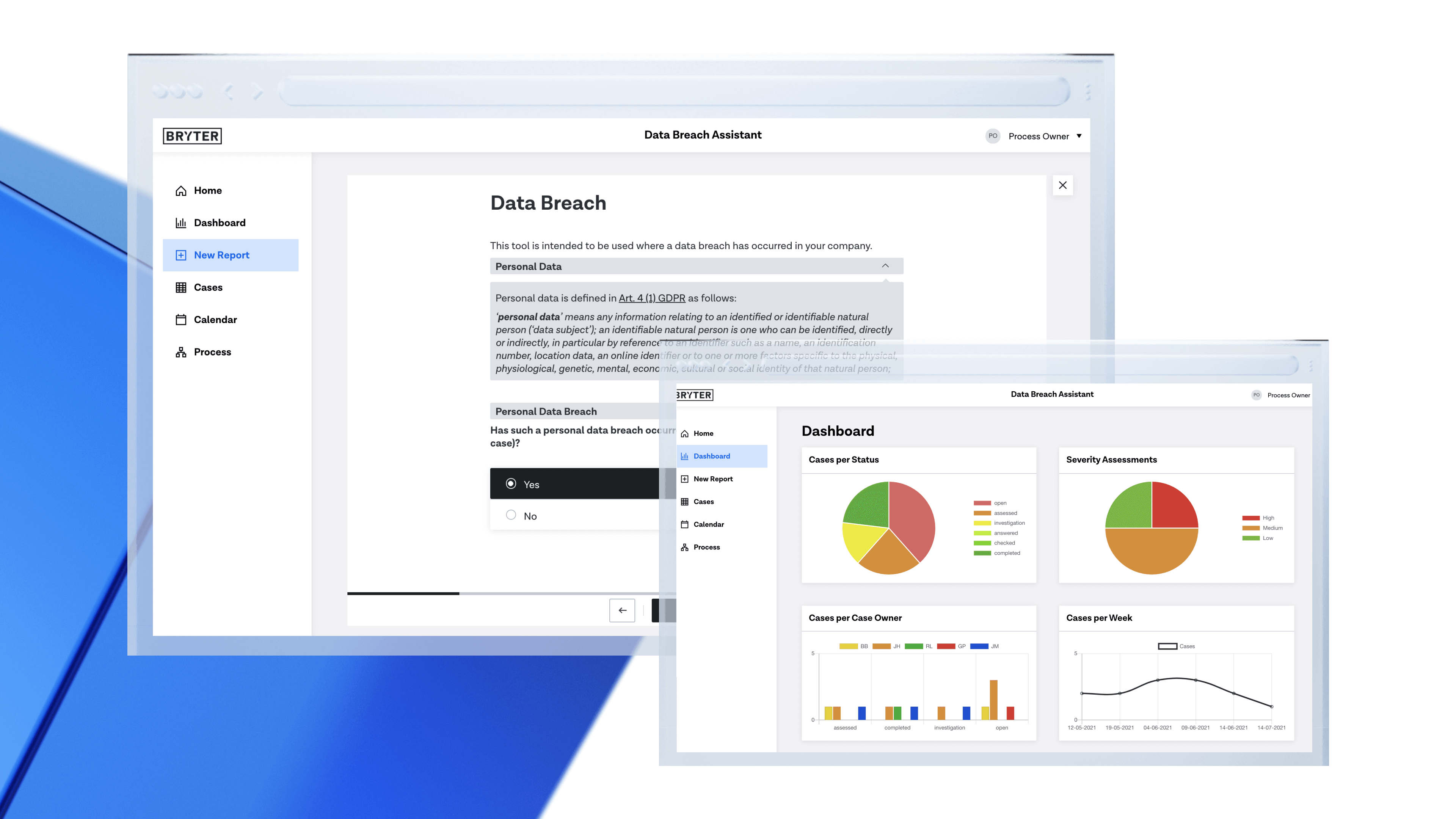
What's the Line Between a Security Breach, and a Data Breach? - DLC Technology Blog | DLC Technology
Cyber attack pixel perfect linear icon. Cybercrime. Deploy malware. Hacking activity. Data breach. Thin line illustration. Contour symbol. Vector outline drawing. Editable stroke. 12726028 Vector Art at Vecteezy



/cdn.vox-cdn.com/uploads/chorus_asset/file/19887730/Breach_E_full_charge.jpg)